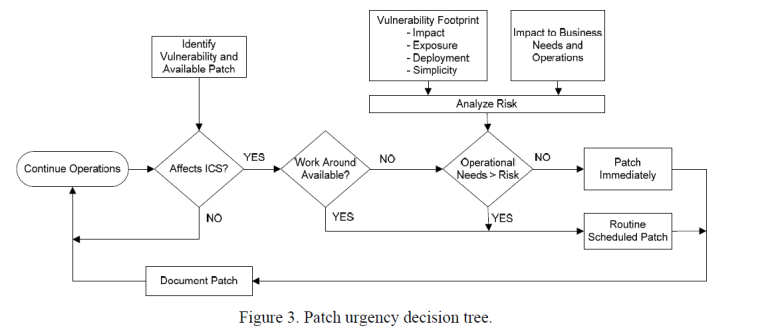
Vulnerability analysis related to patch management is a process of determining when and why a patch should be implemented in the control system. It is recommended that a patch review team should be utilized to assess and determine if an ICS is vulnerable to identified attacks. A method used to determine if an industrial control system is vulnerable to risks is called vulnerability footprint or attack surface.
The vulnerability footprint consists of four primary elements. These include
- Deployment
- Exposure
- Impact
- Simplicity
Here we determine how an asset owner can implement the patch process based on this scenario.
The asset owner has seven communication systems remotely tied to controls with only one server system using a vendor unique protocol. A web search for vulnerabilities regarding this protocol lists several websites. However, the references to US-CERT web pages that list the Vulnerability Notes information of NIST National Vulnerability Database CVE-id information will provide the most reliable data. US-CERT vulnerability notes define the problems, impacts, and solutions with the CVE number for a particular vulnerability.
Deployment
A review of Common Vulnerability and Exposure (CVE) among several informational websites reveals that users of a certain protocol version are vulnerable. However, users of later versions are not susceptible. A quick investigation of the installed version of the protocol would determine immediately if further action is required. If the clean version is installed, all activities can stop as the vulnerability has been addressed. The older version is vulnerable, and the next step is to determine the deployment risk.
Exposure
US-CERT vulnerability footprint review shows the exposure value as high, based on unauthorized access via the network. This data can be utilized to determine the ranking directly, or the asset owner can derive it after reading the report. It helps determine which vulnerability ranks high and needs immediate action as outside exposure means the control system is open to external internet access.
Impact
Assuming that the ability to modify setpoints or general controls does not exist on the system via the vulnerable protocol version, the impact is medium. Another concern regarding unauthorized access is that all linked network systems are vulnerable to cascading failure impacts from one system.
Simplicity
The final analysis is to determine what skills are required to exploit the vulnerability. The exploit required more advanced knowledge, so the ranking can be marked as low. US-CERT would recommend that the asset owner should deploy an updated version immediately.












Post comments (0)