
An essential element in protecting the nation’s critical infrastructure is the security of control systems. Industrial control system or ICS refers to the process control, supervisory control and data acquisition, distributed control, and other systems that monitor, control, and manage a nation’s critical infrastructure. These systems are deployed and leveraged across the world, spanning multiple sectors and industries. Critical Infrastructure and Key Resources consists of transmission systems, electric power generators, dams, and water systems, transmission systems, chemical and petroleum systems, communication systems, and other critical systems that can’t tolerate sudden interruption.
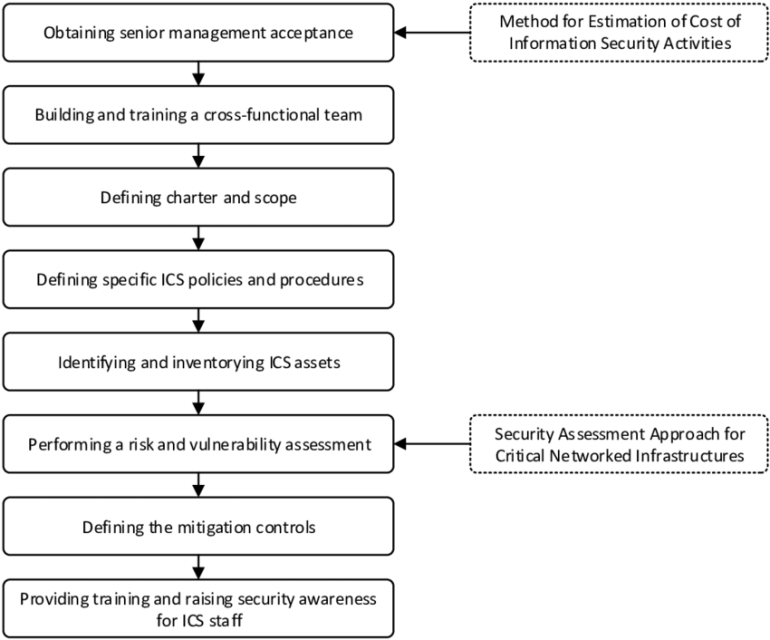
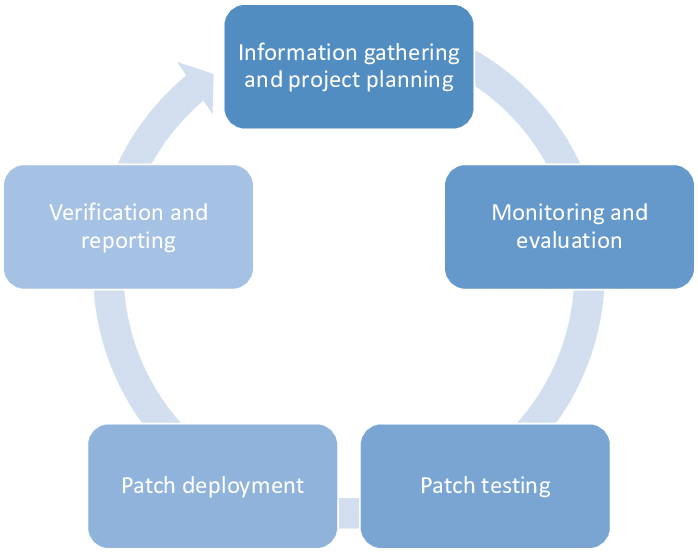
A control system collects information and performs operations based on established parameters and information. The patch management of industrial control systems is essential as it traditionally addresses functionality and stability issues. Patches help resolve functional issues and vulnerabilities in control systems. However, there are various challenges that can complicate patch management. If enterprises do not overcome these challenges, they can’t patch systems efficiently and effectively. There are various security standards designed to help organizations deploy patch management processes, highlight the challenges faced by organizations, and best practices to overcome them.
In this article, we will discuss some major standards for patch management of Industrial control systems, including
- IEC 62443
- NCA
- NIST
- NERC
- UAE-NESA











Post comments (0)