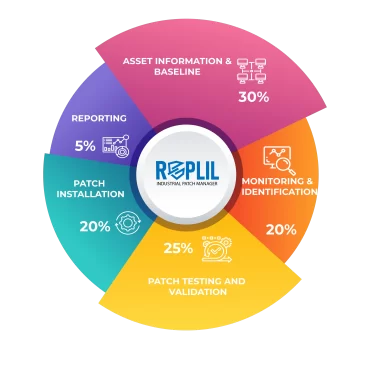
The first step in establishing an effective patch management program is to create a patch management policy. This policy should define the roles and responsibilities of those involved in the patch management process, identify the assets that need to be protected, and outline the patch management process. The policy should be clear and concise and should address the following questions:
- Who is responsible for patch management?
- What is the process for identifying vulnerabilities and patches?
- How are patches tested and deployed?
- How often will the patch management program be reviewed and updated?
Inventory of Hardware and Software Assets
After creating a patch management policy, the next step is to inventory all hardware and software assets. This is necessary to identify what needs to be patched and to ensure that all assets are accounted for in the patch management program. An inventory of assets should include the following:
- Hardware: servers, workstations, laptops, mobile devices, printers, scanners, etc.
- Software: operating systems, applications, utilities, etc.
Vulnerability Assessment
Once the inventory of assets has been completed, the next step is to assess the risks associated with each vulnerability. This will help organizations prioritize which patches to deploy first. Vulnerability assessments can be performed using tools such as vulnerability scanners, which can identify vulnerabilities and assess their severity. The results of vulnerability assessments should be used to create a prioritized list of vulnerabilities to be patched.
Testing Patches
Before deploying patches in a production environment, it is essential to test them in a non-production environment to ensure that they do not cause any unintended consequences. Testing patches can help identify potential issues, such as compatibility issues or conflicts with other software, that can cause problems when deploying patches. Testing patches in a non-production environment also allows organizations to validate the effectiveness of patches in mitigating the identified vulnerabilities.
Deploying Patches
Once patches have been tested, they can be deployed in a production environment. Deploying patches should be done in a controlled and systematic manner to ensure that they are deployed to all relevant systems and that they do not cause any disruptions to critical business functions. The following steps should be taken when deploying patches:
- Deploy patches to a small subset of systems first to ensure that they do not cause any issues.
- Monitor systems for any adverse effects after patch deployment.
- If patches cause any issues, roll them back and investigate the cause of the problem.
- Continue deploying patches to additional systems until all relevant systems have been patched.
Monitoring for New Vulnerabilities and Patches
The final step in establishing an effective patch management program is to monitor systems for new vulnerabilities and patches. New vulnerabilities can emerge at any time, and organizations must be prepared to identify and prioritize new vulnerabilities and patches as they are released. Monitoring for new vulnerabilities and patches can be accomplished through various methods, including:
- Subscribing to vulnerability feeds and alerts from trusted sources.
- Participating in security forums and communities to stay informed of emerging threats and vulnerabilities.
- Regularly reviewing vendor advisories and patch releases.
Regularly Reviewing and Updating the Patch Management Program
The patch management program should be regularly reviewed and updated to ensure that it remains effective over time. This review should include an assessment of the effectiveness of the program in mitigating vulnerabilities and continuous improvement opportunities. The following steps should be taken when reviewing and updating the patch management program:
- Conduct a periodic review of the patch management policy to ensure that it is up-to-date and relevant.
- Re-assess the inventory of hardware and software assets to ensure that all assets are accounted for.
- Review the prioritized list of vulnerabilities and patches to ensure that they are still relevant and that new vulnerabilities have been added to the list.
- Evaluate the effectiveness of the patch management program in mitigating vulnerabilities and addressing cybersecurity risks.
- Analyze the results of vulnerability assessments and patch deployments to identify areas for improvement.